A penetration test, or pen test, finds security weaknesses in systems. It simulates cyberattacks to improve defenses.
But why is this important? In today’s digital age, cyber threats are everywhere. Businesses and individuals face constant risks from hackers. A penetration test helps identify vulnerabilities before attackers do. This proactive approach strengthens security measures. It protects sensitive data and maintains trust.
Companies can understand their weaknesses and fix them. Pen tests also ensure compliance with security standards. They help in building a strong defense against evolving threats. Understanding the purpose of penetration tests is crucial. It empowers organizations to safeguard their digital assets. So, investing in regular pen tests is wise.
Credit: verpex.com
Introduction To Penetration Testing
A penetration test helps identify vulnerabilities in a system. It simulates real-world cyber attacks to find weaknesses. This proactive approach enhances security and protects sensitive data.
In the world of cybersecurity, the question isn’t whether your system will be attacked, but when. That’s where penetration testing comes into play. It’s a proactive approach to uncover vulnerabilities in your network before malicious hackers do. By simulating real-world attacks, penetration testing helps you identify and fix security gaps, keeping your data safe and sound.Defining Penetration Testing
Penetration testing, often called “pen testing,” is a simulated cyberattack on your system. It’s conducted by ethical hackers who mimic the strategies of malicious actors. The goal is to find vulnerabilities that could be exploited. Think of it as hiring a locksmith to test the security of your locks. The ethical hacker doesn’t aim to cause harm but to show you where your defenses might falter. By understanding these vulnerabilities, you can strengthen your security measures.Importance In Cybersecurity
Why is penetration testing crucial in cybersecurity? Simply put, it helps you stay one step ahead of cybercriminals. With new threats emerging constantly, static defenses are not enough. Regular pen testing ensures your security measures evolve with the threats. Consider a company that stored sensitive customer data. A penetration test revealed a weak point in their firewall. Fixing it prevented a potential data breach, saving them from financial and reputational damage. Ask yourself this: Would you rather learn about a security flaw from a friendly tester or a hostile hacker? Pen testing gives you the opportunity to fix issues in a controlled environment. This proactive approach can save you significant trouble down the line.Identifying Vulnerabilities
Identifying vulnerabilities is a crucial aspect of penetration testing in cybersecurity. Imagine your digital world as a fortress; penetration testing is like sending skilled scouts to find cracks in the walls before the attackers do. By understanding these vulnerabilities, you can reinforce your defenses and safeguard your valuable data. This proactive approach helps you stay ahead in the cybersecurity game.
Common Security Flaws
Have you ever wondered where your systems might be vulnerable? Some common security flaws include outdated software, weak passwords, and unpatched systems. These flaws are like open doors for hackers. Keeping your software updated and using strong passwords can reduce these risks significantly.
Another common issue is insufficient encryption. Without proper encryption, sensitive information can be easily intercepted. Think of encryption as a digital lock that keeps your data secure during transmission. Regularly checking encryption protocols ensures your data remains protected.
Evaluating Risk Levels
Once vulnerabilities are identified, evaluating their risk levels is essential. Not all vulnerabilities pose the same threat. Some might be minor annoyances, while others could lead to catastrophic breaches. Prioritizing these risks allows you to focus resources where they’re needed most.
Consider the impact and likelihood of each vulnerability being exploited. Ask yourself: How damaging would it be if this flaw were exploited? How likely is it to happen? This helps you make informed decisions about where to allocate your security efforts.
Your goal is to minimize risk without disrupting operations. Striking this balance ensures your systems remain secure and functional, providing peace of mind in your cybersecurity strategy.
Testing Methodologies
Penetration testing plays a crucial role in cybersecurity. Various methodologies exist to assess system vulnerabilities. Each method offers unique insights. They help identify weaknesses before attackers exploit them. Let’s explore two common testing methodologies: Black Box Testing and White Box Testing.
Black Box Testing
Black Box Testing simulates an external attack. Testers have no prior knowledge of the system. They approach it like real-world hackers would. This method reveals vulnerabilities seen by outsiders. It highlights issues that arise from external threats. The goal is to identify weak points in system defenses. Companies use these findings to strengthen security measures.
White Box Testing
White Box Testing offers a different approach. Testers have full knowledge of the system’s architecture. They examine internal structures and coding practices. This method uncovers hidden vulnerabilities deep within the system. It focuses on logic errors and coding flaws. White Box Testing ensures the system’s internal security is robust. It helps in refining and enhancing code security.
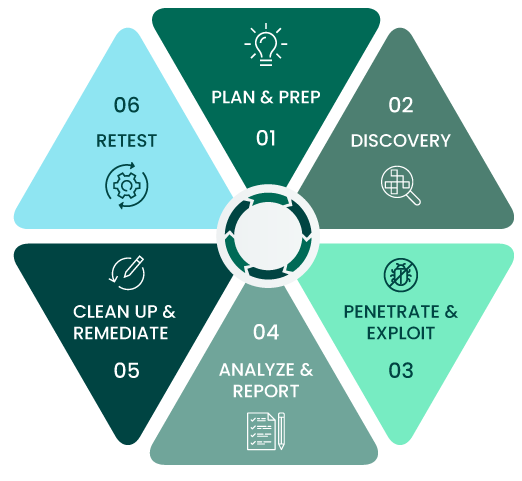
Credit: www.coresecurity.com
Real-world Attack Simulation
Penetration tests aim to find security gaps in systems before hackers do. They simulate real-world cyber attacks. This helps organizations strengthen their defenses and protect sensitive data.
In cybersecurity, penetration testing serves a vital role. It helps organizations identify vulnerabilities. One of the core aspects of this testing is real-world attack simulation. This process mimics potential cyber threats that a company might face. It provides an opportunity to test defenses against actual attacks. Such simulations are crucial in understanding the security posture.Imitating Cyber Threats
Penetration testers imitate cyber threats to find weak spots. They think like hackers and try different attack strategies. This approach helps in understanding how a real attack might unfold. By simulating actual threats, they reveal vulnerabilities before hackers can exploit them. These simulations give companies a clear view of their security gaps.Analyzing Attack Vectors
Analyzing attack vectors is a key part of penetration testing. Testers explore all possible paths an attacker might take. They examine how an attacker could enter and move within a system. This analysis helps identify which systems are most vulnerable. Companies use this information to strengthen their defenses. By understanding attack vectors, organizations can better protect themselves. “`Strengthening Security Posture
In the ever-evolving landscape of cybersecurity, one might wonder how organizations can stay one step ahead of cyber threats. The answer lies in strengthening your security posture, a crucial aspect of safeguarding digital assets. Penetration testing plays a vital role in this process, acting like a friendly sparring partner that helps you identify weaknesses before adversaries do. By simulating attacks, penetration tests reveal vulnerabilities in your defenses, enabling you to patch them up and fortify your security strategies.
Implementing Recommendations
Once a penetration test is completed, you’ll receive a detailed report outlining discovered vulnerabilities. This report is your roadmap to a more secure infrastructure. Implementing the recommendations provided can significantly reduce risk. Think of it as a recipe for a robust defense—each step taken strengthens your system against potential breaches.
Consider this: a colleague once shared how their company avoided a major breach by swiftly applying recommended patches from a penetration test. The lesson here is clear—actionable insights can make or break your security posture.
Enhancing Defensive Strategies
Penetration tests do more than just highlight vulnerabilities. They offer a unique perspective on how your security measures hold up against real-world attacks. This insight is invaluable for refining your defensive strategies. By understanding your weaknesses, you can develop targeted responses that improve resilience.
Ask yourself, how can you turn identified weaknesses into strengths? The key lies in adapting and evolving your tactics. As threats change, so should your defensive strategies. Regular penetration testing ensures your defenses are not just reactive but proactively robust.
Ultimately, the goal is to create a security posture that’s not just strong but agile. One that adapts to threats and continuously improves. Are you ready to enhance your defensive strategies and build a fortress around your digital assets?
Credit: www.blackduck.com
Compliance And Regulation
Compliance and regulation are crucial in cybersecurity. They ensure organizations follow rules and standards. Penetration tests help meet these requirements. This keeps data safe and secure. It also avoids penalties and maintains trust. Let’s explore how penetration tests support compliance.
Meeting Industry Standards
Many industries have strict cybersecurity standards. These protect sensitive information. Penetration tests identify weaknesses in systems. They ensure systems meet these standards. Testing reveals vulnerabilities before they become threats. This proactive approach is essential. It helps businesses stay secure and compliant.
Ensuring Legal Requirements
Legal requirements demand businesses protect data. Breaches can lead to fines or legal action. Penetration tests check if systems follow legal rules. They find gaps in security measures. Fixing these gaps prevents data breaches. This process saves companies from costly penalties. It also boosts customer confidence.
Choosing A Penetration Testing Provider
A penetration test in cybersecurity identifies vulnerabilities in systems before attackers exploit them. It simulates real-world hacking attempts to uncover weaknesses. Choosing a provider ensures your systems are securely assessed, helping to safeguard sensitive information.
Choosing the right penetration testing provider is crucial for your organization’s cybersecurity. A good provider will ensure your systems are thoroughly tested, vulnerabilities are identified, and solutions are recommended to protect your data. But how do you know which provider is the right fit for your needs? Let’s break it down.Evaluating Expertise
Start by assessing the technical skills of potential providers. Do they have certifications that speak to their proficiency, like OSCP or CEH? These qualifications suggest a solid understanding of penetration testing methodologies. Consider their experience in your specific industry. If a provider has worked with businesses similar to yours, they’re more likely to understand your unique challenges and vulnerabilities. Ask them about their testing process. A reputable provider will be transparent about their methods and willing to explain how they plan to test your systems.Assessing Reputation
Look for testimonials and case studies. Do past clients speak highly of their services and results? Positive feedback can indicate reliability and effectiveness. Check online reviews and forums for candid insights. Are there consistent complaints or praise? This can give you a more balanced view of their performance. Network with peers in your industry to see if they’ve worked with the provider. Personal recommendations can be invaluable and often provide insights you won’t find online. Choosing the right penetration testing provider is not just about finding someone who can do the job. It’s about partnering with a team that understands your needs, has the right expertise, and comes highly recommended. Are you confident in your current provider, or is it time to explore other options?Future Of Penetration Testing
The future of penetration testing is rapidly evolving. As technology progresses, so do the methods used to protect it. Penetration testing plays a vital role in identifying vulnerabilities. It helps businesses safeguard their digital assets.
Emerging Technologies
Emerging technologies are reshaping penetration testing. Tools powered by artificial intelligence (AI) make testing faster. They provide deeper insights into potential threats. Blockchain technology also influences penetration testing. It offers new ways to secure and verify data. These advancements help testers identify and address weaknesses efficiently.
Evolving Threat Landscape
The threat landscape constantly changes. Cybercriminals adapt quickly, finding new ways to exploit systems. Penetration testing must stay ahead of these threats. Regular updates and new strategies are necessary. This proactive approach ensures vulnerabilities are identified early.
Frequently Asked Questions
What Is The Main Purpose Of A Penetration Test?
A penetration test identifies security vulnerabilities in a system. It simulates cyberattacks to assess how easily threats can bypass defenses. This helps improve security measures, ensuring data protection and compliance with standards. Regular testing maintains robust cybersecurity against evolving threats.
What Is The Purpose Of Standard Penetration Test?
The standard penetration test evaluates soil density and strength. It helps determine foundation stability for construction projects. Engineers use it to assess load-bearing capacity and identify potential issues in soil layers. Accurate data ensures safe and efficient building designs.
How Important Is Penetration Testing In Cybersecurity?
Penetration testing is crucial for identifying vulnerabilities in cybersecurity systems. It helps strengthen defenses against potential threats. Regular testing ensures systems are secure and compliant with industry standards. By simulating attacks, organizations can proactively address weaknesses, reducing the risk of data breaches and enhancing overall security posture.
What Is The Purpose Of A Penetration Test Report And What Does It Provide?
A penetration test report identifies security vulnerabilities and assesses their impact. It provides detailed findings, risk levels, and remediation recommendations. This report helps organizations strengthen their cybersecurity posture and safeguard sensitive data. Understanding vulnerabilities enables proactive defense against potential threats.
Conclusion
Penetration tests are crucial in strengthening cybersecurity. They identify system vulnerabilities. By simulating attacks, they reveal weak spots. This helps companies fix potential threats. Businesses can protect sensitive data better. Regular tests ensure the security measures stay effective. Cyber threats evolve constantly.
Continuous testing keeps defenses updated. Investing in penetration tests is smart. It saves costs from potential breaches. Building trust with clients becomes easier. They feel safer knowing their data is secure. In the digital age, staying ahead of hackers is vital.
Penetration tests offer that edge. Keep your systems robust and secure.
{ “@context”: “https://schema.org”, “@type”: “FAQPage”, “mainEntity”: [ { “@type”: “Question”, “name”: “What is the main purpose of a penetration test?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “A penetration test identifies security vulnerabilities in a system. It simulates cyberattacks to assess how easily threats can bypass defenses. This helps improve security measures, ensuring data protection and compliance with standards. Regular testing maintains robust cybersecurity against evolving threats.” } } , { “@type”: “Question”, “name”: “What is the purpose of standard penetration test?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “The standard penetration test evaluates soil density and strength. It helps determine foundation stability for construction projects. Engineers use it to assess load-bearing capacity and identify potential issues in soil layers. Accurate data ensures safe and efficient building designs.” } } , { “@type”: “Question”, “name”: “How important is penetration testing in cybersecurity?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “Penetration testing is crucial for identifying vulnerabilities in cybersecurity systems. It helps strengthen defenses against potential threats. Regular testing ensures systems are secure and compliant with industry standards. By simulating attacks, organizations can proactively address weaknesses, reducing the risk of data breaches and enhancing overall security posture.” } } , { “@type”: “Question”, “name”: “What is the purpose of a penetration test report and what does it provide?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “A penetration test report identifies security vulnerabilities and assesses their impact. It provides detailed findings, risk levels, and remediation recommendations. This report helps organizations strengthen their cybersecurity posture and safeguard sensitive data. Understanding vulnerabilities enables proactive defense against potential threats.” } } ] }