White box penetration testing offers deep insights into system vulnerabilities. It involves examining internal structures, code, and design.
This type of test is crucial for identifying weaknesses that are often hidden from plain view. Understanding the key properties of a white box penetration test helps in evaluating its effectiveness. This testing method goes beyond superficial assessments. It provides a thorough examination of security flaws within a system’s architecture.
Unlike black box testing, white box testing requires access to source code and design documents. This access allows testers to explore deeper into the system’s inner workings. Knowing these key properties empowers organizations to fortify their defenses. White box penetration testing reveals vulnerabilities that might be overlooked with other testing methods. By uncovering these weaknesses, it enhances overall security measures and safeguards sensitive data.
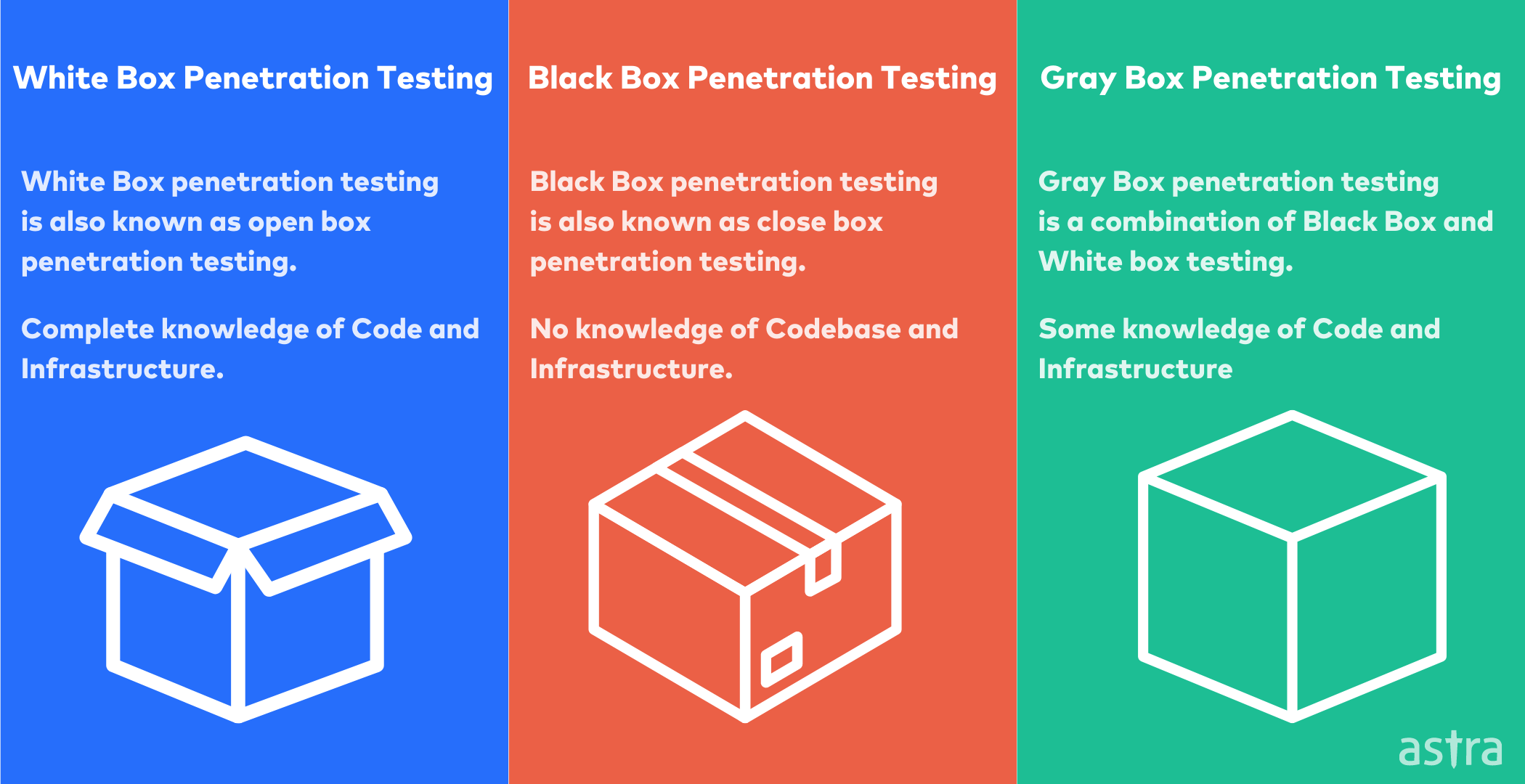
Credit: www.getastra.com
White Box Testing Basics
White box penetration testing focuses on code structure, logic, and design. It requires deep knowledge of the system’s internal workings. Testers identify vulnerabilities by examining code paths, data flow, and control structures.
Understanding the basics of white box testing is crucial for anyone interested in cybersecurity. This form of testing is like having a backstage pass to your own systems, allowing you to see everything from the inside. It provides a comprehensive view that helps identify weaknesses before they can be exploited by malicious actors.Purpose And Scope
White box testing focuses on examining the internal workings of a system or application. It allows testers to see the source code, design, and architecture. This insight helps them evaluate how well the components work together and pinpoint any vulnerabilities. The scope of a white box penetration test is broad. It can include reviewing code for security flaws, testing specific functions, or assessing the overall security posture of an application. By knowing what’s happening inside, you can address potential threats more effectively.Role In Security
White box testing plays a vital role in enhancing security. It’s not just about finding bugs; it’s about understanding the system’s behavior under various conditions. This knowledge allows you to strengthen defenses and ensure your application runs smoothly and securely. Think of it as a proactive measure. Instead of waiting for an attack, you’re actively seeking out and fixing weak spots. This approach can save time, money, and protect your reputation. Have you ever considered how secure your system truly is? With white box testing, you get the clarity needed to confidently answer that question. It’s a strategic investment in your security infrastructure, offering peace of mind in an increasingly complex digital landscape.
Credit: www.spiceworks.com
Core Techniques
In the realm of cybersecurity, understanding how to carry out a white box penetration test effectively is crucial. This type of test offers a transparent view of the system’s architecture, allowing you to examine every nook and cranny for vulnerabilities. The core techniques used in white box testing are essential to ensure a thorough evaluation. But what exactly do these techniques involve, and how can they improve your security posture?
Source Code Analysis
Source code analysis is a fundamental aspect of white box penetration testing. You dive deep into the actual code of the application or system, scrutinizing it for weaknesses. This technique allows you to identify coding errors, insecure practices, and potential backdoors that might be exploited by attackers.
Imagine being able to pinpoint a flaw in the code before it becomes a real-world issue. This proactive approach can save you from a security nightmare. During one of my white box tests, I discovered a vulnerability that could have exposed sensitive user data. Fixing it preemptively was a relief, both for me and the organization.
Configuration Review
Configuration review is another crucial technique in white box testing. It involves examining system settings and configurations to ensure they’re secure. Misconfigurations can lead to severe security breaches, making this step indispensable.
Consider the impact of a misconfigured firewall or improper database permissions. These issues might seem minor but can open the door to attackers. During a test, I once found a misconfiguration that allowed unauthorized access to critical system files. Correcting this configuration avoided potential disaster.
Do you regularly review your configurations to ensure they align with security best practices? If not, it’s time to start, because this proactive measure can prevent vulnerabilities from slipping through the cracks.
Tool Selection
Tool selection plays a vital role in white box penetration testing. Choosing the right tools can make or break the test. It ensures thorough security assessment of your systems. The right mix of automated and manual tools enhances test accuracy. This section explores both types of tools in detail.
Automated Tools
Automated tools save time by quickly scanning through code. They identify common vulnerabilities like SQL injection or cross-site scripting. These tools usually offer a comprehensive overview of potential security issues. Automated scanners can sift through large codebases efficiently.
Such tools are great for repetitive tasks. They offer consistent results without human error. You can integrate them into your development pipeline easily. Some popular options include static analysis tools and vulnerability scanners.
Manual Techniques
Manual techniques involve a hands-on approach by skilled testers. These techniques are crucial for finding complex vulnerabilities. Such issues might be missed by automated tools. Human intuition and expertise play a significant role here.
Manual testing includes code reviews and logic flaw identification. Testers may also simulate real-world attack scenarios. This approach allows for a deeper understanding of the system’s security posture. It fills gaps left by automated solutions.
Vulnerability Identification
Vulnerability identification is a core aspect of white box penetration testing. This process seeks to uncover potential security weaknesses in a system. By examining source code and system architecture, testers can identify flaws. These flaws could be entry points for cyber threats. The goal is to find vulnerabilities before malicious actors do.
Common Vulnerabilities
Common vulnerabilities are often the first targets during a penetration test. These include SQL injection, cross-site scripting, and buffer overflow. Each of these can cause significant harm if exploited. SQL injection allows unauthorized database access. Cross-site scripting can steal user information. Buffer overflow may cause system crashes or data corruption. Identifying these vulnerabilities early can prevent major security breaches.
Advanced Threats
Advanced threats present a greater challenge in vulnerability identification. These threats often involve sophisticated techniques and tools. Attackers may use zero-day exploits or advanced persistent threats. Such threats require a deeper understanding of the system. It involves analyzing complex interactions within software and hardware. Advanced threats often target specific weaknesses unique to a system. Detecting these requires expertise and comprehensive testing methodologies.
Security Assessments
Security assessments play a vital role in safeguarding digital assets. A white box penetration test offers a comprehensive view of a system’s vulnerabilities. It allows testers to evaluate the security from an insider’s perspective. This method helps identify potential risks and impacts effectively.
Risk Evaluation
Risk evaluation is crucial in a white box test. It involves analyzing the system’s components thoroughly. Testers examine code, configurations, and architecture. This detailed inspection helps pinpoint weak spots. It highlights areas vulnerable to attacks. Understanding these risks aids in developing stronger defenses.
Impact Analysis
Impact analysis assesses the potential consequences of security breaches. It evaluates how vulnerabilities affect business operations. Testers simulate attacks to gauge their effects. This analysis helps prioritize security measures. Businesses can then focus on critical areas needing protection. The insights gained drive informed decision-making.
Reporting Findings
The culmination of a white box penetration test lies in reporting findings. This step is crucial for understanding vulnerabilities and planning improvements. Clear documentation and effective communication are vital here. They ensure all stakeholders grasp the results and their implications. Let’s explore these aspects in more detail.
Documentation Practices
Documentation practices capture every detail of the penetration test. They include detailed logs of each test conducted. These logs provide a comprehensive view of all vulnerabilities discovered. They also show the steps taken during the tests. Proper documentation ensures traceability and accountability. It aids in future audits and reviews. Well-organized reports are essential for effective follow-up actions.
Communication Strategies
Effective communication strategies convey findings clearly to stakeholders. Use simple language to explain technical terms. This helps non-experts understand the implications of vulnerabilities. Visual aids like charts and graphs can simplify complex data. Regular meetings with stakeholders ensure everyone is on the same page. Open channels for queries and feedback enhance understanding and collaboration.
Mitigation Strategies
Mitigation strategies in a white box penetration test are crucial for strengthening your organization’s cybersecurity defenses. They offer actionable insights into how to patch vulnerabilities and enhance security controls. When these strategies are effectively implemented, they significantly reduce the risk of cyber threats and ensure the protection of sensitive data.
Patch Management
Patch management involves regularly updating software to fix vulnerabilities that hackers could exploit. It’s like maintaining your car—you wouldn’t skip an oil change, right? Neglecting software updates can lead to serious security breaches.
Consider setting up automated patching systems. This ensures that your software stays up to date without relying on manual intervention. Automated systems can save you time and reduce human error, minimizing the risk of vulnerabilities.
Do you remember the last time you had to manually update every single application? It was tedious, wasn’t it? Automation can help you avoid that hassle while keeping your systems secure.
Security Controls
Security controls are mechanisms that protect your systems from unauthorized access and threats. Think of them as the locks on your doors. Would you leave your front door unlocked overnight?
Implement multi-factor authentication. This adds an extra layer of security by requiring multiple forms of verification before granting access. It’s like asking for an ID and a password before letting someone in.
Consider conducting regular security audits. These audits can identify weaknesses in your existing controls and suggest improvements. Have you ever conducted an audit and found unexpected gaps? It’s better to find them yourself than to let a hacker exploit them.
Effective mitigation strategies are about being proactive and prepared. What steps will you take today to strengthen your cybersecurity? Remember, the goal is to stay one step ahead of potential threats.
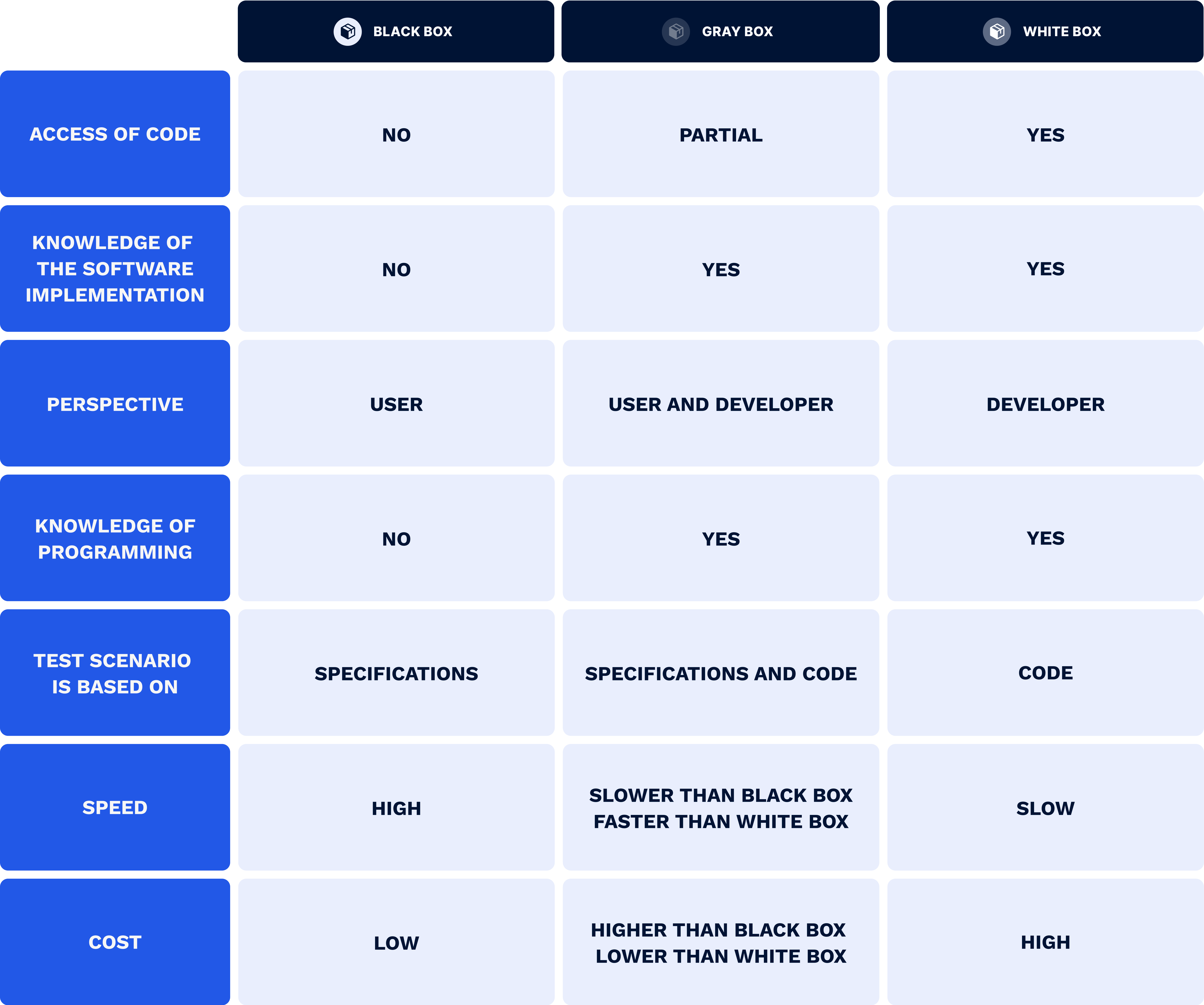
Credit: www.effectivesoft.com
Challenges And Solutions
White box penetration testing presents unique challenges. Understanding these hurdles helps testers develop effective solutions. This approach requires deep insight into a system’s architecture. The aim is to find vulnerabilities from within. Addressing complexities and resource demands is crucial. With thorough planning, testers can overcome these challenges.
Complexity Issues
White box testing involves intricate systems. Detailed knowledge of code and architecture is required. Testers must understand every component’s role. This complexity can lead to missed vulnerabilities. Simplifying this process is essential. Break down systems into manageable sections. Focus on critical areas first. Use automated tools to assist in analysis. This reduces human error.
Resource Allocation
Effective resource management is key. White box tests need skilled professionals. They require time and effort. Prioritize tasks to allocate resources wisely. Set clear objectives. Determine which areas need more focus. Balance team workload to maintain efficiency. Ensure testers have the right tools. Proper equipment speeds up the testing process.
Budget constraints can limit testing scope. Plan carefully to maximize available funds. Use open-source tools when possible. This lowers costs without sacrificing quality. Ensure continuous communication within the team. Share insights and findings regularly. This keeps everyone informed and aligned. Proper coordination enhances test results.
Frequently Asked Questions
What Is A Key Characteristic Of White Box Testing Techniques?
White box testing techniques focus on internal code structure and logic. Testers examine code paths, branches, and statements. This approach ensures code quality by identifying hidden errors. It requires knowledge of programming and aims to improve code efficiency and security.
White box testing provides thorough code coverage for enhanced software reliability.
What Is The Main Objective Of A White Box Penetration Test?
The main objective of a white box penetration test is identifying vulnerabilities with full access to the internal code. It helps in assessing security risks by examining code, architecture, and internal systems. This approach ensures comprehensive analysis, leading to more effective strategies for enhancing cybersecurity measures.
What Are Key Areas For A Penetration Test?
Key areas for a penetration test include network security, application security, and physical security. Assess wireless networks, databases, and servers. Evaluate access controls and data protection. Test for vulnerabilities in web applications and APIs. Ensure compliance with security standards and best practices.
What Are The Advantages Of White Box Penetration Testing?
White box penetration testing offers comprehensive security evaluation. It identifies vulnerabilities by accessing source code and internal structures. This method ensures thorough coverage, faster detection, and detailed insights into potential exploits. It enhances security by simulating real-world attack scenarios, allowing organizations to address weaknesses effectively and improve overall system resilience.
Conclusion
White box penetration testing offers deep insights into security systems. It examines internal structures and access points, enhancing security protocols effectively. This method identifies vulnerabilities that might be missed otherwise. With detailed access to code and architecture, testers find potential risks.
Organizations gain a clearer view of their security landscape. This approach supports proactive defense strategies. It ensures systems are resilient against threats. Implementing white box testing strengthens overall cybersecurity. Regular testing is crucial to stay ahead of cyber threats. A robust security posture protects valuable data and maintains trust.
{ “@context”: “https://schema.org”, “@type”: “FAQPage”, “mainEntity”: [ { “@type”: “Question”, “name”: “What is a key characteristic of white box testing techniques?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “White box testing techniques focus on internal code structure and logic. Testers examine code paths, branches, and statements. This approach ensures code quality by identifying hidden errors. It requires knowledge of programming and aims to improve code efficiency and security. White box testing provides thorough code coverage for enhanced software reliability.” } } , { “@type”: “Question”, “name”: “What is the main objective of a white box penetration test?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “The main objective of a white box penetration test is identifying vulnerabilities with full access to the internal code. It helps in assessing security risks by examining code, architecture, and internal systems. This approach ensures comprehensive analysis, leading to more effective strategies for enhancing cybersecurity measures.” } } , { “@type”: “Question”, “name”: “What are key areas for a penetration test?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “Key areas for a penetration test include network security, application security, and physical security. Assess wireless networks, databases, and servers. Evaluate access controls and data protection. Test for vulnerabilities in web applications and APIs. Ensure compliance with security standards and best practices.” } } , { “@type”: “Question”, “name”: “What are the advantages of white box penetration testing?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “White box penetration testing offers comprehensive security evaluation. It identifies vulnerabilities by accessing source code and internal structures. This method ensures thorough coverage, faster detection, and detailed insights into potential exploits. It enhances security by simulating real-world attack scenarios, allowing organizations to address weaknesses effectively and improve overall system resilience.” } } ] }