Penetration testing, ethical hacking, and red teaming are key cybersecurity practices. Each serves a unique purpose in securing systems and data.
Understanding their differences helps businesses protect themselves from threats. Penetration testing simulates attacks to find vulnerabilities in systems. Ethical hacking uses similar techniques but focuses on improving security. Red teaming takes it further, challenging defenses in real-world scenarios. These methods are crucial for organizations to understand and improve their security posture.
Comparing them helps businesses choose the right strategy for their needs. Each approach offers distinct benefits and insights. Knowing which suits your goals can enhance your security efforts. Let’s delve deeper into these practices to understand their roles in safeguarding your digital assets.

Credit: www.mindpointgroup.com
Penetration Testing
Penetration testing is the secret weapon in the cybersecurity arsenal. Imagine being tasked with finding the hidden vulnerabilities in a system, much like a detective piecing together clues to solve a mystery. It’s not just a skill; it’s an art form that requires precision, insight, and an understanding of the hacker’s mindset. But what truly sets penetration testing apart?
Definition And Scope
Penetration testing is all about simulating attacks on your systems to find weaknesses before someone else does. You become the ‘friendly hacker’, working to ensure the security of your digital fortress. But don’t think of it as just poking around. It’s a structured approach with a clear purpose.
Its scope can vary widely. Some tests focus on specific areas, like your web applications, while others take a broader view of your entire network. The ultimate goal is to identify vulnerabilities that could be exploited, giving you a chance to fix them before they become a real threat.
Typical Methodologies
Penetration testing is not a one-size-fits-all activity. Different methodologies guide how you approach the task. The most common is the black box testing, where you start with no prior knowledge of the system. It’s like stepping into unknown territory, which makes it thrilling yet challenging.
Then there’s white box testing, where you have all the information about the system. Imagine having the map before entering a maze; it’s insightful but requires you to be thorough in your exploration. Lastly, gray box testing combines elements of both, offering a balanced approach.
Have you ever wondered what it feels like to be the person responsible for uncovering security flaws? The adrenaline rush of discovering a vulnerability can be addictive, but remember, the end game is to protect and secure. So, what methodology would you choose to safeguard your digital assets?
Penetration testing is more than just finding flaws; it’s about understanding the potential threats and preparing for them. As you delve into this realm, keep your ultimate goal in mind: fortifying your defenses against the unseen. Are you ready to become the detective your cybersecurity needs?
Red Teaming
Red Teaming involves simulating real-world attacks to test security systems, contrasting with penetration testing, which focuses on identifying vulnerabilities. Ethical hacking aims to safeguard systems by finding and fixing weaknesses. Each has distinct goals, methods, and scopes in cybersecurity, enhancing overall protection.
Red Teaming is a powerful security strategy. It’s designed to test the resilience of an organization’s defense systems. Unlike traditional security tests, Red Teaming mimics real-world threats. This approach helps identify vulnerabilities that may be overlooked. It involves a team of skilled professionals who act as attackers. They simulate complex cyber-attacks to expose weaknesses in your security structure.Definition And Scope
Red Teaming is more than just penetration testing. It’s a full-scale attack simulation. The scope extends beyond digital systems. It includes physical security and human elements too. This comprehensive approach examines every aspect of security. The goal is to identify gaps and improve overall defense mechanisms.Tactics And Techniques
Red Teaming employs advanced tactics and techniques. These mimic sophisticated cyber threats. Social engineering is a key element. It tricks employees into revealing sensitive information. Physical intrusion tests evaluate security controls like locks and alarms. Cyber attacks target network vulnerabilities and software weaknesses. These techniques help organizations prepare for real-world attacks.Goals And Objectives
Understanding the distinct goals and objectives of penetration testing, ethical hacking, and red teaming is crucial. Each approach serves a unique purpose in cybersecurity. Knowing these differences helps organizations choose the right strategy to protect their assets. Let’s delve into the specific goals and objectives of these methods.
Penetration Testing Goals
Penetration testing aims to find security flaws in systems and networks. The goal is to identify vulnerabilities before attackers do. This process helps organizations fix weak points in their security. Pen testers simulate real-world attacks to test defenses. They focus on specific systems or applications. The ultimate aim is to ensure systems are secure and resilient.
Red Teaming Objectives
Red teaming adopts a broader approach than penetration testing. It simulates an attacker’s mindset to test entire security systems. The objective is to assess how well defenses stand against sophisticated attacks. Red teams often test an organization’s detection and response capabilities. They aim to improve overall security posture by identifying gaps. This approach helps organizations prepare for real-world cyber threats.
Approaches And Strategies
Understanding the different approaches and strategies in cybersecurity can be complex. Penetration testing, ethical hacking, and red teaming each have unique methods. These practices protect systems and data from potential threats. They require different skills and tactics to ensure robust security.
Penetration Testing Approach
Penetration testing seeks vulnerabilities in a system. A tester simulates an attack on the network. The goal is to find weak points. This helps businesses understand their security gaps. It’s often a focused, time-bound exercise. Testers use various tools to mimic potential threats. They provide a report detailing vulnerabilities found. This allows companies to fix issues before real attacks occur.
Red Teaming Strategy
Red teaming involves a more comprehensive strategy. It tests the entire security posture of an organization. The approach is holistic, simulating a real-world attack. A red team tries to breach defenses without being detected. They use creative and unexpected methods. This helps in understanding how attackers could exploit systems. Red teaming also evaluates the response of security teams. It offers a broader view of security effectiveness.
Tools And Techniques
When diving into the world of cybersecurity, understanding the tools and techniques is crucial for differentiating between penetration testing, ethical hacking, and red teaming. Each approach employs unique methods to assess security vulnerabilities, but the way they do it can vary significantly. Let’s explore these differences further and see what sets them apart.
Penetration Testing Tools
Penetration testing often utilizes tools designed to simulate real-world attacks. These tools help identify vulnerabilities in systems, applications, and networks. Commonly used tools include:
- Metasploit: A framework that allows testers to discover, exploit, and validate vulnerabilities.
- Nmap: A network scanning tool that identifies hosts and services on a computer network.
- Burp Suite: Used for web application security testing, enabling testers to intercept, modify, and replay web requests.
Each of these tools serves a specific purpose, but collectively they form a powerful arsenal for penetration testers. Have you ever wondered how often these tools find vulnerabilities that were previously overlooked?
Red Teaming Techniques
Red teaming goes beyond mere tool usage, embracing a variety of techniques to mimic advanced persistent threats (APTs). This approach is less about tools and more about strategy and creativity.
- Social Engineering: Tricking individuals into divulging confidential information, testing human vulnerabilities.
- Physical Breach Attempts: Gaining unauthorized physical access to facilities to test security protocols.
- Advanced Tactics: Using custom scripts and hacking techniques tailored to bypass specific defenses.
Red teaming is all about thinking like a hacker. It’s not just about breaking in; it’s about doing it without being noticed. How would you approach a scenario where conventional methods fail?
These tools and techniques are more than just technical jargon—they’re the frontline in defending against cyber threats. Whether you’re a seasoned professional or new to cybersecurity, understanding how each method operates is key to building robust defenses. Have you considered which approach best fits your organization’s needs?
Benefits And Limitations
Understanding the differences between penetration testing, ethical hacking, and red teaming is crucial. Each approach offers unique benefits and faces distinct limitations. Knowing these helps organizations protect their digital assets effectively.
Advantages Of Penetration Testing
Penetration testing focuses on identifying vulnerabilities in systems. It simulates attacks to find weak spots before real threats exploit them. This helps organizations strengthen their security measures.
Test results provide detailed insights into potential risks. Companies can prioritize fixing issues based on the severity identified. This proactive approach reduces the chance of costly data breaches.
Regular penetration tests ensure systems remain secure over time. They adapt to new threats as they emerge in the cybersecurity landscape.
Limitations Of Red Teaming
Red teaming provides a comprehensive security assessment. But it requires significant time and resources. This makes it less suitable for smaller organizations with limited budgets.
Red teaming can be disruptive to normal operations. Its realistic approach might cause temporary system slowdowns or interruptions.
Due to its complexity, red teaming needs skilled professionals. A shortage of such expertise can pose challenges for some organizations.
Choosing The Right Approach
Understanding the difference between penetration testing, ethical hacking, and red teaming is crucial. Penetration testing identifies vulnerabilities in a system. Ethical hacking focuses on defending against cyber threats. Red teaming simulates real-world attacks to test defenses. Each approach plays a unique role in cybersecurity.
Choosing the right approach between penetration testing, ethical hacking, and red teaming can feel like navigating a maze. Each strategy serves a specific purpose, and choosing incorrectly can waste resources or leave vulnerabilities unchecked. Understanding the nuances of each can help you make informed decisions that align with your organization’s objectives. ###Factors To Consider
Consider the scope of your project. Penetration testing is usually more focused, examining specific applications or networks. If your goal is to identify vulnerabilities in a particular system, this might be your best bet. Ethical hacking offers a broader approach. It involves a variety of techniques to test the security of your entire infrastructure. If you need a comprehensive assessment, ethical hacking can provide insights into your overall security posture. Red teaming is about emulating real-world threats. It’s the most exhaustive option, simulating attacks from advanced adversaries. Choose red teaming if you’re interested in understanding how your defenses hold up against sophisticated threats. ###Organization Needs
Ask yourself: What are the specific security challenges your organization faces? If compliance is a concern, penetration testing might align with regulatory requirements. For organizations aiming to foster a culture of continuous improvement, ethical hacking can identify weaknesses and suggest improvements across the board. This approach supports long-term security resilience. If your organization handles sensitive data and needs to prepare for advanced threats, red teaming should be on your radar. It’s a rigorous test of your defenses, offering a reality check on your current security measures. Involve your team in the decision. Discussing the potential benefits and limitations of each approach can lead to a more strategic decision. Tailor the security strategy to fit your unique needs rather than adopting a one-size-fits-all mindset. Choosing the right approach is not just about addressing immediate issues. It’s about aligning with your long-term security goals and protecting your organization’s future.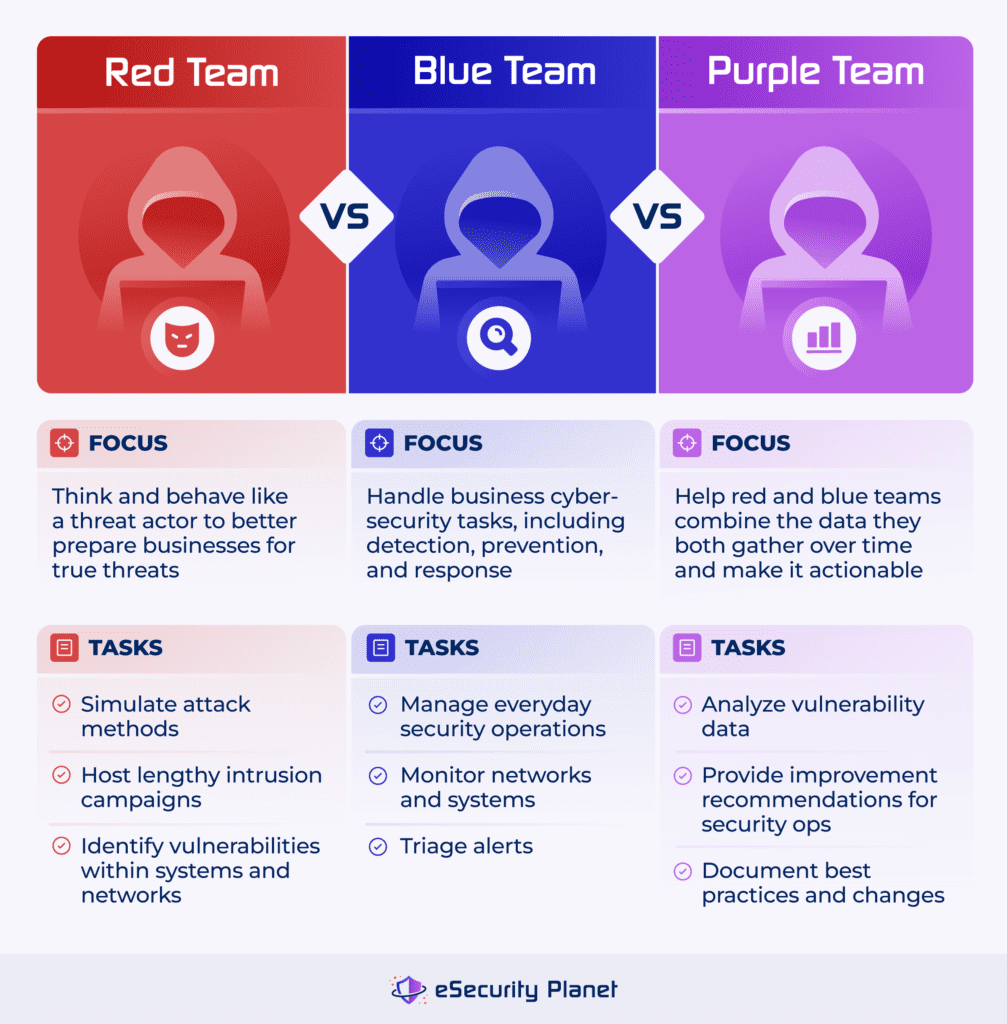
Credit: www.esecurityplanet.com
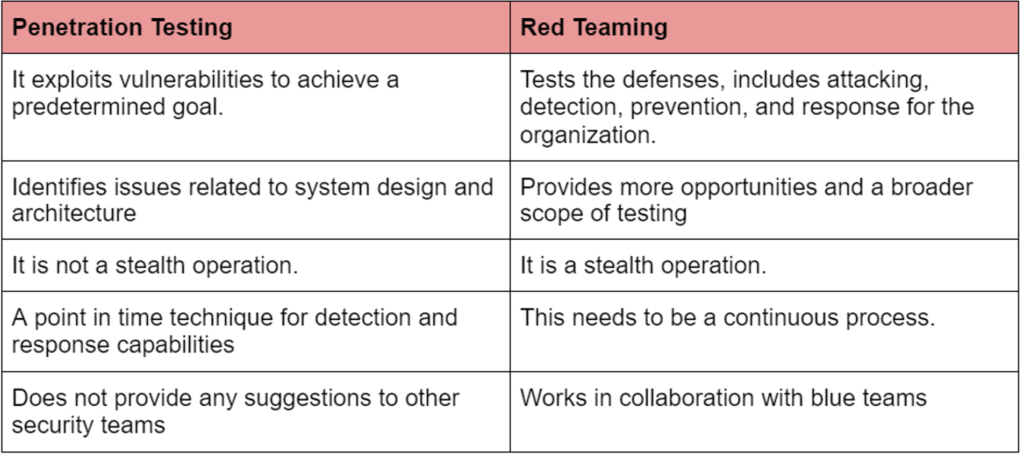
Credit: www.firecompass.com
Frequently Asked Questions
What Is The Difference Between Red Teaming And Penetration Testing?
Red teaming assesses security by simulating real-world attacks, testing defenses comprehensively. Penetration testing identifies vulnerabilities in specific systems or applications. Red teaming is broader, while penetration testing focuses on finding technical flaws. Both aim to strengthen cybersecurity but differ in scope and objectives.
What Is The Difference Between Ethical Hacking And Red Teaming?
Ethical hacking focuses on identifying vulnerabilities in systems. Red teaming simulates real-world attacks to test security measures. Ethical hackers work independently, while red teams collaborate to challenge defenses. Both aim to improve cybersecurity but differ in approach and scope.
What Is The Difference Between Penetration Testing And Ethical Hacking?
Penetration testing is a structured security assessment focusing on specific vulnerabilities. Ethical hacking involves broader security practices, identifying potential threats across systems. Both aim to enhance security but differ in scope and methodology.
What Is The Main Difference Between Va And Pt?
The main difference between VA and PT lies in their roles. Virtual Assistants (VA) handle administrative tasks remotely, like scheduling and communication. Physical Therapists (PT) focus on rehabilitating patients through exercises and treatments. VA work is digital, while PT involves direct patient interaction in healthcare settings.
Conclusion
Understanding these security practices strengthens your digital defenses. Penetration testing finds vulnerabilities in your systems. Ethical hacking tests security measures and protects data. Red teaming simulates real-world attacks to assess readiness. Each approach offers unique insights. Choosing the right one depends on your needs.
Enhance your cybersecurity with these strategies. Stay informed. Protect your assets. Embrace a proactive security approach. Keep learning about these methods. Your digital safety depends on it.
{ “@context”: “https://schema.org”, “@type”: “FAQPage”, “mainEntity”: [ { “@type”: “Question”, “name”: “What is the difference between red teaming and penetration testing?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “Red teaming assesses security by simulating real-world attacks, testing defenses comprehensively. Penetration testing identifies vulnerabilities in specific systems or applications. Red teaming is broader, while penetration testing focuses on finding technical flaws. Both aim to strengthen cybersecurity but differ in scope and objectives.” } } , { “@type”: “Question”, “name”: “What is the difference between ethical hacking and red teaming?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “Ethical hacking focuses on identifying vulnerabilities in systems. Red teaming simulates real-world attacks to test security measures. Ethical hackers work independently, while red teams collaborate to challenge defenses. Both aim to improve cybersecurity but differ in approach and scope.” } } , { “@type”: “Question”, “name”: “What is the difference between penetration testing and ethical hacking?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “Penetration testing is a structured security assessment focusing on specific vulnerabilities. Ethical hacking involves broader security practices, identifying potential threats across systems. Both aim to enhance security but differ in scope and methodology.” } } , { “@type”: “Question”, “name”: “What is the main difference between VA and PT?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “The main difference between VA and PT lies in their roles. Virtual Assistants (VA) handle administrative tasks remotely, like scheduling and communication. Physical Therapists (PT) focus on rehabilitating patients through exercises and treatments. VA work is digital, while PT involves direct patient interaction in healthcare settings.” } } ] }