Penetration testing is a crucial cybersecurity measure. It simulates attacks to find system vulnerabilities.
This testing helps protect sensitive information from hackers and cyber threats. In today’s digital age, security is vital for everyone. Businesses, governments, and individuals store vast amounts of data online. With cybercrime on the rise, ensuring that this data remains safe is essential.
Penetration testing identifies weak spots before criminals can exploit them. It helps organizations understand their security gaps and fix them proactively. This process not only protects data but also builds trust with clients and stakeholders. Understanding the importance of penetration testing can empower you to safeguard your digital assets effectively. Let’s explore how this form of testing works and why it is a key component of cybersecurity strategies.
Credit: qawerk.com
Introduction To Penetration Testing
Penetration testing identifies security weaknesses in computer systems by simulating cyber attacks. It helps protect sensitive data from hackers. Testing ensures systems are strong and secure, preventing unauthorized access.
In today’s digitally driven world, ensuring the security of your online presence is crucial. Cyber threats loom large, and businesses must take proactive measures to protect themselves. One effective method is penetration testing, a practice that simulates cyber-attacks to identify vulnerabilities in your systems. This isn’t just a technical exercise; it’s a vital part of your cybersecurity strategy.Purpose And Goals
The primary aim of penetration testing is to identify security weaknesses before malicious hackers can exploit them. By simulating real-world attacks, penetration testers can provide a clear picture of potential threats. They don’t just spot vulnerabilities; they also offer practical insights on how to fix these issues. Penetration testing helps prioritize security efforts. It highlights which vulnerabilities pose the greatest risk, allowing you to allocate resources effectively. This targeted approach ensures you address the most critical issues first, enhancing your overall security posture.Importance In Cybersecurity
Incorporating penetration testing into your cybersecurity framework is not just a best practice; it’s essential. It offers a proactive defense against cyber threats that can lead to data breaches and financial losses. By identifying weaknesses early, you can prevent costly damages and safeguard your reputation. Consider this: a single undetected vulnerability can lead to a massive data breach. Penetration testing acts as a safety net, catching these vulnerabilities before they become a problem. It’s an investment in peace of mind, knowing your systems are as secure as possible. As you think about your cybersecurity strategy, ask yourself: Are you doing enough to protect your digital assets? Penetration testing provides the insights you need to stay one step ahead of potential attackers, ensuring your business remains secure in an ever-evolving threat landscape.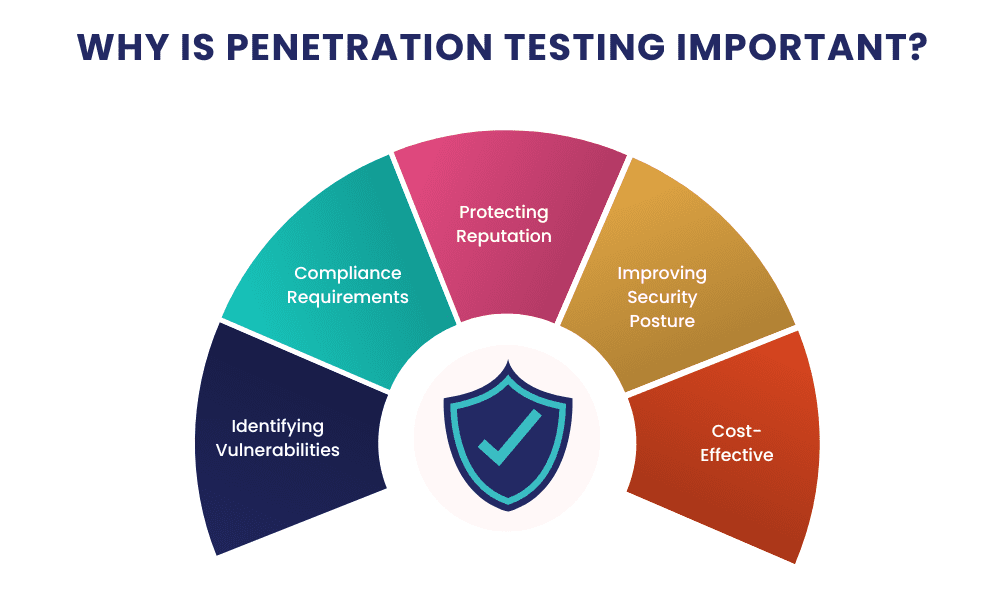
Credit: nextdynamix.com
Types Of Penetration Testing
Penetration testing helps identify security weaknesses in systems and networks. There are various types of penetration tests. Each type has a unique focus. They uncover vulnerabilities from different perspectives.
External Testing
External testing targets a company’s external assets. These include websites, servers, and network infrastructure. The goal is to simulate attacks from outside the organization. External testers mimic real-world cyber threats. They seek vulnerabilities in publicly exposed systems. This type of testing reveals how easy it is for outsiders to breach security.
Internal Testing
Internal testing examines security from inside the network. This simulates an attack by a malicious insider. Or a hacker who gained access through phishing. Internal testers assess the risk of internal threats. They explore vulnerabilities within firewall-protected systems. This testing helps strengthen defenses against internal breaches.
Penetration Testing Process
Penetration testing, or ethical hacking, assesses a system’s security by simulating cyberattacks. Identifying vulnerabilities helps prevent real attacks, protecting sensitive data and systems. This process is crucial for maintaining robust cybersecurity defenses.
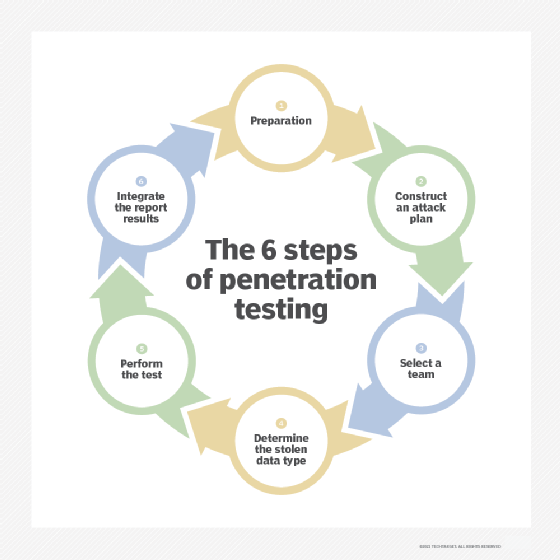
The penetration testing process is a systematic approach to evaluating the security of a system by simulating a cyber attack. This process helps identify vulnerabilities before malicious hackers can exploit them. Understanding the steps involved can empower you to better protect your digital assets. Let’s dive into the key phases of this process. ###Planning And Reconnaissance
Planning and reconnaissance form the foundation of a successful penetration test. During this phase, testers gather as much information as possible about the target system. This could involve collecting data like IP addresses, domain details, and network structures. A well-prepared plan outlines the scope and goals of the test. It defines what systems will be tested and identifies any specific threats to focus on. By having a clear strategy, you ensure that the testing process is efficient and effective. Imagine you are a detective piecing together clues to solve a mystery. The more information you gather upfront, the better your chances of uncovering hidden issues. This phase is about understanding your target to tailor your approach. ###Scanning And Exploitation
The scanning phase involves using tools to identify potential vulnerabilities in the system. Testers employ automated software to scan for weaknesses like open ports, outdated software, and misconfigurations. This step is crucial because it highlights the system’s weak spots that need attention. Once potential vulnerabilities are identified, testers move to the exploitation phase. Here, they attempt to exploit these weaknesses to gain unauthorized access or control. This is done safely to avoid any real damage to the system. Think of this phase as a practice drill for real-world attacks. By exploiting vulnerabilities, you can see how an attacker might breach your defenses. It’s like testing your home security by trying to pick the lock—better to find out it’s weak before a burglar does. Each phase of the penetration testing process plays a vital role in securing your systems. By understanding these steps, you take proactive measures to strengthen your defenses. How secure is your digital environment today?Tools And Techniques
Penetration testing evaluates security by simulating cyber attacks on systems. It identifies vulnerabilities before real threats occur. Businesses use these tests to protect sensitive data and ensure robust cybersecurity measures.
Penetration testing, often referred to as “pen testing,” is a crucial process used to identify vulnerabilities in a system before malicious hackers can exploit them. To effectively carry out this testing, a combination of tools and techniques is employed. Understanding these can help you appreciate how penetration testing safeguards your digital assets.Automated Tools
Automated tools are the backbone of penetration testing. They speed up the process by quickly scanning for known vulnerabilities. Think of them as your first line of defense. Tools like Nmap and Nessus are popular choices. Nmap helps in network discovery and security auditing, while Nessus is excellent for detecting vulnerabilities. These tools can save you time and provide a comprehensive overview of your system’s security posture. But remember, automated tools aren’t foolproof. They might miss complex vulnerabilities that require a human touch. This is where manual techniques come into play.Manual Techniques
Manual techniques involve the hands-on expertise of a skilled tester. These methods dive deeper into the system to uncover vulnerabilities that automated tools might overlook. Imagine having a seasoned detective on the case. They don’t just rely on the obvious; they look at the subtleties. For example, a tester might manually probe for logic flaws in an application or attempt to bypass authentication mechanisms. Manual testing requires a keen eye and experience. It’s about thinking like a hacker and anticipating their moves. This approach often uncovers hidden flaws that could be disastrous if left unchecked. Have you ever wondered if a combination of both automated tools and manual techniques might be the best approach? Many experts believe that using both provides a more robust security assessment. Balancing speed with depth ensures that no stone is left unturned in securing your system.Common Vulnerabilities Exploited
Penetration testing reveals how attackers might exploit system vulnerabilities. These tests identify weaknesses that could lead to data breaches. Understanding common vulnerabilities helps protect sensitive information.
Software Bugs
Software bugs are errors in a program’s code. They create potential security risks. Attackers exploit these bugs to gain unauthorized access. Many software bugs stem from coding mistakes. Even small errors can create significant vulnerabilities. Keeping software updated helps fix these bugs.
Developers release patches to address known issues. Regular updates can prevent exploitation. Testing software thoroughly before release reduces the risk of bugs. Penetration tests simulate attacks to find these vulnerabilities.
Configuration Flaws
Configuration flaws arise from improper system settings. These flaws can expose sensitive data. Default settings often create security gaps. Attackers exploit these gaps to access systems.
Misconfigured firewalls and open ports are common issues. Regular audits can identify configuration flaws. Correct settings enhance security and protect data. Penetration tests help discover these flaws before attackers do.
Benefits Of Penetration Testing
Penetration testing identifies security weaknesses in a system before hackers can exploit them. It helps organizations strengthen their defenses. Regular testing ensures data safety and compliance with industry standards, protecting sensitive information effectively.
Penetration testing, often called pen testing, is a powerful tool in the cybersecurity arsenal. It simulates real-world attacks on your systems to uncover vulnerabilities before malicious hackers do. But why should you care about penetration testing? Understanding its benefits is crucial for anyone looking to safeguard their digital assets.Risk Reduction
Penetration testing helps you identify weak points in your security before they become entry points for cybercriminals. Imagine discovering a vulnerability that could have led to a data breach—before it happens. By proactively finding and fixing these gaps, you significantly reduce the risk of unauthorized access to your systems. Think of it as a dress rehearsal for a potential cyber attack. You get to see how your defenses hold up without the real-world consequences. This proactive approach not only protects your data but also saves you from potential financial and reputational damage.Compliance Assurance
Many industries are bound by strict regulations to protect sensitive information. Penetration testing ensures that your organization meets these compliance standards. Whether it’s GDPR, HIPAA, or PCI-DSS, failing to comply can result in hefty fines and legal issues. Regular pen tests provide documented proof of your security measures. This is invaluable during audits, showing that you’re committed to protecting your clients’ data. It also builds trust with customers and partners who know you take security seriously. Are you confident that your systems would pass a compliance audit today? Penetration testing can give you that peace of mind. It’s not just about avoiding penalties; it’s about demonstrating responsibility and integrity in handling data.Challenges In Penetration Testing
Penetration testing is a crucial aspect of maintaining robust cybersecurity defenses. However, it comes with its own set of challenges that testers and organizations must navigate. These challenges can impact the effectiveness and outcomes of penetration tests, making it essential to understand and address them.
Technical Limitations
Despite advancements in technology, penetration testing tools are not foolproof. You might encounter limitations in tools that fail to identify complex vulnerabilities. Older systems and networks can also pose challenges due to compatibility issues.
Consider the evolving nature of cyber threats. Attackers are always ahead with new tactics. This means your testing tools need constant updates to keep pace. Are your tools up to date, or are they lagging behind?
Real-world testing environments can be unpredictable. Simulated attacks might not replicate actual scenarios. How do you ensure your tests reflect true vulnerabilities in your systems?
Ethical Considerations
Penetration testing involves probing systems for weaknesses. This can sometimes blur the lines between ethical and unethical actions. You need clear guidelines to ensure ethical boundaries are respected.
Imagine discovering sensitive data during a test. How do you handle such information responsibly? You must have protocols in place to prevent misuse or data breaches during testing.
Consent is crucial. You must have explicit permission from stakeholders before testing. Without this, you risk legal complications. Are your processes transparent and ethical?
Addressing these challenges head-on ensures that penetration testing not only identifies vulnerabilities but also upholds the integrity and trust of your cybersecurity practices. Are you ready to tackle these challenges effectively?
Future Of Penetration Testing
The future of penetration testing is evolving rapidly. Cyber threats grow more sophisticated, demanding advanced defense measures. As technology advances, penetration testing adapts to meet new challenges. This ensures robust security for businesses and individuals alike.
Emerging Threats
Every day, cybercriminals develop new attack methods. These evolving threats require constant vigilance. Penetration testing helps in identifying vulnerabilities before hackers exploit them. This proactive approach is essential in maintaining digital safety. Organizations must stay ahead to protect sensitive data from potential breaches.
Advanced Technologies
Technological advancements transform penetration testing methods. Automation tools streamline testing processes, saving time and resources. Artificial intelligence and machine learning enhance threat detection capabilities. These technologies help identify patterns and predict potential attacks. Cloud-based testing services offer scalable solutions for diverse needs. They ensure comprehensive security across various platforms.
Credit: www.techtarget.com
Frequently Asked Questions
What Is The Importance Of A Penetration Test?
Penetration tests identify security vulnerabilities in systems, helping prevent data breaches. They enhance cybersecurity measures, ensuring compliance with industry standards. Regular testing protects sensitive information and maintains trust with clients. Conducting these tests can save businesses from financial losses and reputational damage.
Effective penetration testing supports robust security strategies.
What Is The Main Goal Of Penetration Testing?
Penetration testing aims to identify security vulnerabilities in a system. It helps organizations protect sensitive data. Experts simulate cyberattacks to test defenses. This process strengthens security measures and mitigates risks. Regular testing ensures systems are robust against evolving threats. It is crucial for maintaining cybersecurity and safeguarding digital assets.
What Are The 5 Stages Of Pentesting?
The five stages of pentesting are: 1. Planning and reconnaissance: Gather information about the target. 2. Scanning: Identify open ports and vulnerabilities. 3. Gaining access: Exploit vulnerabilities to access the system. 4. Maintaining access: Ensure persistence within the system. 5.
Analysis and reporting: Document findings and provide recommendations.
What Is The Most Important Part Of A Penetration Test?
Identifying vulnerabilities is the most crucial part of a penetration test. This helps prioritize security improvements and mitigate risks. Effective reporting ensures clear communication of findings and actionable recommendations. Comprehensive testing enhances system security by revealing weaknesses before cybercriminals exploit them.
Regular penetration tests are essential for robust cybersecurity.
Conclusion
Penetration testing plays a crucial role in cybersecurity. It helps identify security gaps. These tests protect sensitive data from cyber threats. Businesses can safeguard their systems effectively. Regular testing ensures systems remain secure. Security measures must evolve with threats. Organizations need to stay proactive.
Penetration testing strengthens security strategies. It builds trust with clients and partners. Implementing these tests boosts confidence in digital safety. Every business should prioritize cybersecurity. Protecting data is essential in today’s digital world. Penetration testing is key to maintaining security.
Stay ahead of cyber threats. Secure your business with regular testing.
{ “@context”: “https://schema.org”, “@type”: “FAQPage”, “mainEntity”: [ { “@type”: “Question”, “name”: “What is the importance of a penetration test?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “Penetration tests identify security vulnerabilities in systems, helping prevent data breaches. They enhance cybersecurity measures, ensuring compliance with industry standards. Regular testing protects sensitive information and maintains trust with clients. Conducting these tests can save businesses from financial losses and reputational damage. Effective penetration testing supports robust security strategies.” } } , { “@type”: “Question”, “name”: “What is the main goal of penetration testing?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “Penetration testing aims to identify security vulnerabilities in a system. It helps organizations protect sensitive data. Experts simulate cyberattacks to test defenses. This process strengthens security measures and mitigates risks. Regular testing ensures systems are robust against evolving threats. It is crucial for maintaining cybersecurity and safeguarding digital assets.” } } , { “@type”: “Question”, “name”: “What are the 5 stages of pentesting?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “The five stages of pentesting are: 1. Planning and reconnaissance: Gather information about the target. 2. Scanning: Identify open ports and vulnerabilities. 3. Gaining access: Exploit vulnerabilities to access the system. 4. Maintaining access: Ensure persistence within the system. 5. Analysis and reporting: Document findings and provide recommendations.” } } , { “@type”: “Question”, “name”: “What is the most important part of a penetration test?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “Identifying vulnerabilities is the most crucial part of a penetration test. This helps prioritize security improvements and mitigate risks. Effective reporting ensures clear communication of findings and actionable recommendations. Comprehensive testing enhances system security by revealing weaknesses before cybercriminals exploit them. Regular penetration tests are essential for robust cybersecurity.” } } ] }